When popular large file transfer services Aspera, GoAnywhere, and MOVEit were hacked in the summer of 2023, it led to a cascading series of data breaches among customers of those services.
Indeed, some of the effects of what TechCrunch called “the biggest hack of the year” are still being discovered several months later.
But the incident highlighted something else: The importance of ensuring you and your people know how to share files securely.
Want a few pointers on implementing secure file transfer practices? Then you’ve come to the right place.
Table of Contents
Secure Large File Transfers for Video
MASV is trusted by global media organizations to transfer large media files securely.
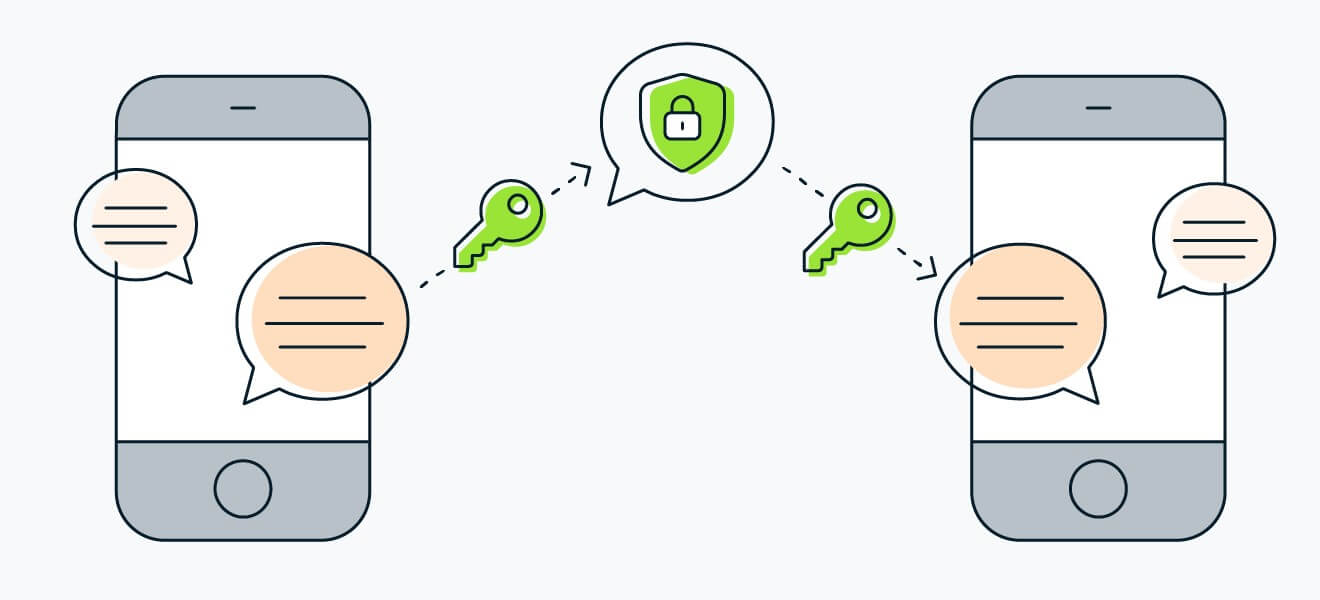
What is Secure File Transfer?
Secure file transfer is the process of transferring files privately and securely to ensure data confidentiality and availability, allowing only the intended recipient to have access to that data.
Private file sharing is imperative when transferring sensitive data such as:
- Personally identifiable information (PII)
- Personal health information (PHI)
- Valuable intellectual property (IP) such as proprietary datasets or unreleased video footage.
Secure file sharing software usually includes security features such as encryption, identity access management (IAM) controls, password protection on file transfers, and file tracking capabilities. Individuals and businesses can take additional steps to secure their content, such as forensic watermarking and other techniques.
How to Send Files Securely: 5 Best Practices
Organizations can’t just implement secure file-sharing software and call it a day, however. From multi factor authentication (MFA) to strong passwords, the most secure way to transfer files means ensuring your software is up to snuff while adhering to a set of file-sharing security best practices.
1. Secure and Encrypted Connections
Any network that shares sensitive data needs to be secured with an encrypted connection. Secure connections are encrypted by one or more security protocols. They ensure data security by encrypting all data packets that leave the network.
Insecure connections allow bad actors to easily penetrate networks and access sensitive data using data packet sniffer software or similar tools.
For example, websites can have both secure and insecure connections. Secure websites are protected by a Secure Sockets Layer (SSL) and will have the “https://” prefix. Google Chrome identifies secure sites by displaying a padlock icon to the left of the URL. At the same time, insecure sites display “http://”.
Regarding data transfer, the most secure offerings include file-sharing encryption (E2EE), which encrypts data at the source and ensures only the recipient can decrypt it through a unique decryption key.

2. Secure Cloud Services
One of the most significant advantages of popular public clouds such as AWS is their inherent security compared to private clouds or self-hosted (on-prem) systems. While a self-hosted system just down the hall may feel more secure, secure cloud services are far superior in this regard thanks to automatic updates and patches.
Indeed, many organizations often delay implementing these critical patches and updates by weeks, months, or even years because they’re so busy. That makes their data much more vulnerable than on a public cloud platform.
Public clouds also have more resources and time to secure physical data centers and back that up with thousands of security employees who are responsible for keeping your cloud environment secure. If something goes wrong, cloud providers have more resources to spend on disaster recovery (instead of your IT team doing it all on their own).
3. Strong Passwords
The rise of credential stuffing, brute force, and similar cyberattacks means strong passwords are no longer a nice-to-have. They are imperative to ensure data security.
Weak or compromised passwords are among the most common ways cybercriminals gain access to accounts and networks.
Tip: Avoid sharing passwords internally. It simply creates another channel for bad actors to obtain access to a password.
Just one security breach can lead to a cascading series of issues if cybercriminals post compromised passwords on sites such as Pastebin or on the dark web.
The generation and use of strong passwords must be part of your internal security culture. A password management tool can be handy for remembering multiple complex passwords.
4. Multi Factor Authentication
Just like strong passwords, employing identity access management (IAM) functionality such as MFA (also known as two-factor authentication or 2FA) is essential.
Implementing MFA is important because stolen or weak passwords are at the root of around 80% of security breaches. MFA is an essential part of a zero-trust network because it enables networks and systems to verify a person is who they say they are, typically via a phone call or text to their registered mobile device, even if they present the correct password.
5. Ease of Use
By now, we’ve established just how important it is to use an encrypted file sharing solution. But it goes deeper than that. The platform itself needs to be easy to use. If not, it can lead to mistakes by employees which increases the chance of human error when following security transfer protocols.
A secure file sharing platform should have a simple interface that’s as easy as sending an email. That way, even non-technical users can feel confident securely sharing files without risking the transfer of sensitive information to the wrong person or organization.
Stay Compliant with MASV
MASV is compliant under SOC 2 Type II, GDPR, PIPEDA, TPN (Gold Shield), and other data protection regulations.
Why is it Important to Use a Secure File Sharing Platform?
In an environment of constantly escalating IT security threats, a secure file sharing solution is imperative to keep data safe, especially in a bring-your-own-device (BYOD) environment.
Additionally, the rise of shadow IT infrastructure within companies means employees often try to use consumer-grade software when working with sensitive data.
But there are some very specific reasons why organizations must keep file transfers secure. Here are some of the most important:
Privacy and Confidentiality
Organizations have a duty to protect confidential information such as PII, PHI, and other personal or otherwise sensitive data and IP. Robust data privacy allows individuals to control their personal data, including how their data is collected, stored, used, and shared.
Meanwhile, data breaches resulting from shoddy security practices can lead to financial loss, identity theft, and other undesirable outcomes. We all know how damaging the Sony Pictures hack was a few years ago.
Compliance
Hand-in-hand with data privacy and confidentiality is regulatory compliance, which exists primarily in the data protection world to ensure the former. Healthcare and financial organizations have well-established compliance requirements: Serious breaches of the Health Insurance Portability and Accountability Act (HIPAA), for example, can result in fines of up to $1.5M and five years in prison.
Other international data protection regulations include:
- General Data Privacy Regulation (GDPR) (EU)
- Personal Information Protection and Electronic Documents Act (PIPEDA) (Canada)
- California Consumer Privacy Act (CCPA)
- Connecticut Data Privacy Act (CTDPA)
- Act on Protection of Personal Information (APPI) (Japan)
- General Data Protection Law, or Lei Geral de Proteção de Dados (LGPD) (Brazil)
- Personal Data Protection Act (PDPA) (Singapore)
- Personal Data Protection Act (PDPA) (Thailand)
- Personal Data Protection Bill (PDPB) (India)
- Notifiable Data Breach (NDB) Scheme (Australia)
Malicious Actors
Industry watchers have long maintained that more than two dozen records are stolen every second of every day due to cyberattacks. That’s why keeping bad actors away from sensitive data is Job #1 for businesses or individuals who share files.
But keeping information secure has become increasingly tricky as bad guys become more sophisticated through AI and other advanced hacking tools. The stakes for organizations are immense: Along with potential fines and loss of customer trust, companies who allow data breaches due to cyberattacks often face lawsuits from angry (former) customers.
Trust
Trust is an incredibly important factor that often determines customer loyalty. Trust factors such as integrity and ability are crucial for companies and affect a range of customer outcomes, from purchase intent to brand loyalty.
Unfortunately, even if a data breach or cyberattack isn’t an organization’s fault, it usually shatters trust among its customers (and even employees). One study found that nearly 70% of data breach victims lose trust in the breached organization. And once lost, trust can be difficult, if not impossible, to regain.
Secure File Sharing Tools and Services
If you’re wondering how to conduct a secure file upload or send a secure file, look no further than the list of encrypted file share applications below.
- MASV: Best secure file sharing app for large files and enterprise media workflows.
- Dropbox: Secure file sharing between small teams and businesses.
- Google Drive: Secure file sharing and cloud storage that allows users to store, access, and share online files.
- TitanFile: Enterprise-grade secure file transfer and client collaboration platform.
- Internxt Send: Encrypted file sharing service that allows users to securely share documents and photos.
- Signal: Secure file sharing through a chat messenger similar to SMS.
Source: Avast
- SyncThing: Open-source P2P file sync application similar to Resilio Sync in that it uses the BitTorrent protocol.
- GnuPG: Open-source, command-line application that uses the OpenPGP encryption standard to protect emails.
Other secure file sharing tools include the Secure File Transfer Protocol (SFTP), or secure FTP, and File Transfer Protocol Secure (FTPS), which can be used via FTP software such as FileZilla. SFTP is fully encrypted while FTPS as an encrypted layer to the legacy FTP protocol.
The Best Secure Managed File Transfer Solution
Knowing how to send files securely is important but can be overwhelming considering the sheer number of managed file transfer solutions on the market today.
Whichever secure file sharing software you choose, review its security practices closely to ensure your data stays confidential.
If you work with copyrighted media, MASV is one of the most secure cloud file transfer platforms available today thanks to its robust security features. Here’s how it adheres to the five best practices mentioned above:
- Encryption: MASV secures all file transfers in-flight with TLS 1.2 and at-rest with AES-256 encryption.
- Cloud security: MASV operates on the AWS secure cloud platform, a secure-by-design architecture that comes with 300-plus cloud security tools that enable seamless and effective security automation and end-to-end organizational security.
- Strong Passwords: We enforce our users to use a 12-character password for their account, with special characters and upper/lowercase alphabet. We also offer password-protection on each and every transfer and train our staff in password-related best practices.
- Multi Factor Authentication: Any admin login attempt into our network requires MFA, crypto keys, or token-based authentication. We also enable our users to enforce MFA on Team accounts to further prevent unauthorized access to sensitive files.
- Ease of Use: MASV’s browser- and desktop app user interface is as easy to use as sending an email. That means even non-technical employees, contractors, partners, and other collaborators can start sending files with no training or tutorials.
To top it all off, we hold third-party certifications from the Trusted Partner Network (TPN) Gold Shield, ISO 27001, and SOC 2 to verify our legitimacy.
Try our secure file-sharing platform today. You can start for free and get free transfer credits every month.
Stay Compliant with MASV
MASV is compliant under SOC 2 Type II, GDPR, PIPEDA, TPN (Gold Shield), and other data protection regulations.